Previous
Signs That Your Systems May Have Been Compromised
Welcome to a four-part series exploring the common cyber threats within the Caribbean and how to strengthen your organization's resilience by preparing for them.
The COVID-19 pandemic, rapid adoption of cloud-based technologies, advanced interconnectivity, and advances in the uses of emerging technologies such as Artificial Intelligence have all contributed to the evolution of the cyber threat landscape. As a result, cybersecurity threats, as well as the sophistication, complexity, and scale of cyber-attacks, are increasing.
It is estimated that by 2025, the cost of cybercrime is expected to reach $10.5 trillion USD. Damage and destruction of data, stolen money, lost productivity, intellectual property theft, personal and financial data theft, embezzlement, fraud, post-attack disruption to normal business operations, forensic investigations, restoration and deletion of hacked data and systems, and reputational harm are all included in this cost (Cybersecurity Ventures).
So first, let's define a threat. A threat, as defined by the National Institute of Standards and Technology, is any circumstance or event that has the potential to adversely impact organizational operations, assets, or individuals through a system via unauthorized access, destruction, disclosure, modification of data, or denial of service. Organizational threats can arise from numerous sources, both internal and external. Hostile governments, terrorist groups, hacktivists, and cybercriminals are examples of external threat actors. Similarly, internal threat actors can be intentional (e.g., malicious employees) or unintentional (e.g., user or administrator error). Because of their trusted position, internal threat actors can pose a significant threat. Insider threats are often regarded as one of the most likely causes of breaches and are often difficult to detect. In 2021, Latin America and the Caribbean experienced over 289 million cyber-attack attempts, a 600% increase from the prior year, naming the Log4J vulnerability, distributed denial of service (DDOS) attacks, ransomware, phishing campaigns, malwares and trojans, as the top cyber threats observed. (FortiGuard Labs Report 2021).
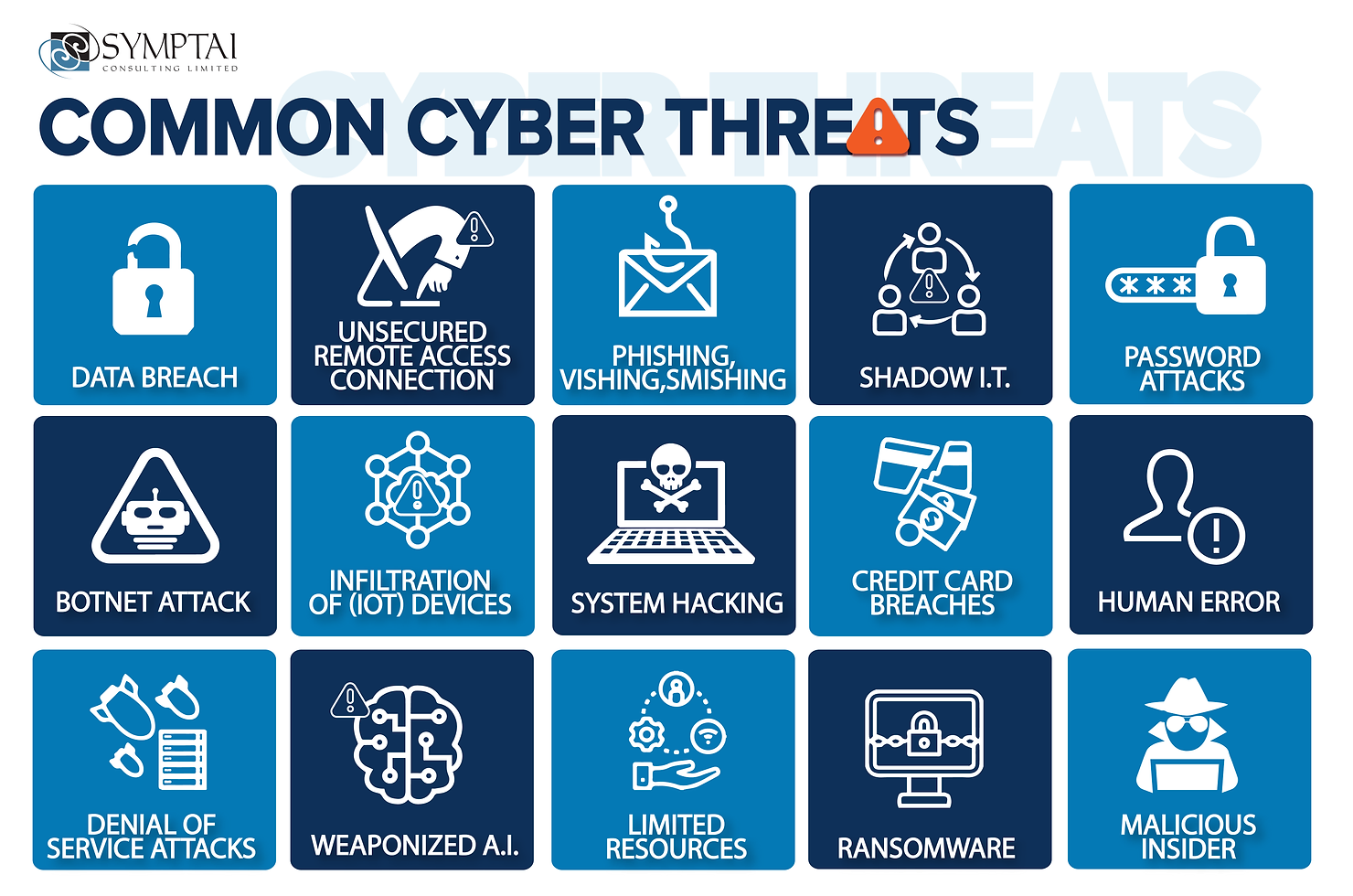
Other common cyber threats include:
Data breaches
Password attacks
Improperly configured systems
Malicious insiders
Human error
Weaponized artificial intelligence
Limited resources
Infiltration of IoT devices
Botnet attacks
System hacking
As an organization, you can no longer afford to treat cybersecurity as an afterthought. Now, more than ever, you are required to balance a rapidly evolving cybersecurity and privacy threat landscape against your own business requirements. As a result, understanding the cyber threat landscape is critical to ensure that your organization is prepared. I am glad you took the time to read through our introduction to cyber threats but as this is intended to be an ongoing conversation I invite you to join me in Part 2 where we will discuss the risks associated with external threats.